HTB Challenge - BabyEncryption
HTB Category: Crypto
HTB Difficulty: Very Easy
Challenge Description
You are after an organised crime group which is responsible for the illegal weapon market in your country. As a secret agent, you have infiltrated the group enough to be included in meetings with clients. During the last negotiation, you found one of the confidential messages for the customer. It contains crucial information about the delivery. Do you think you can decrypt it?
Overview
This challenge contains two files: chall.py and msg.eng. The latter is a string of hex characters, and the former is a python script that presumably generated this ciphertext.
import string
from secret import MSG
def encryption(msg):
ct = []
for char in msg:
ct.append((123 * char + 18) % 256)
return bytes(ct)
ct = encryption(MSG)
f = open('./msg.enc','w')
f.write(ct.hex())
f.close()
Solution
The encryption (or more accurately: obsfucation) here appears straightforward…except for the modulo 256 operation. Somebody better at math than I am could probably reverse this operation, however I’m going to sidestep the problem.
We can see from chall.py that there is no secret key, and we have the operation used to “encrypt” the message. Knowing this, we can simply generate the ciphertext equivalent for each ASCII character and create a lookup table. Once that’s done, it’s just a matter of comparing each ciphertext byte to this table and printing its plaintext equivalent.
import string
import sys
def encryption(msg):
ct = []
for char in msg:
ct.append((123 * ord(char) + 18) % 256)
return bytes(ct).hex()
# Iterate through each ASCII character and figure out what its ciphertext equivalent is
lookupTable = {}
for char in string.printable:
lookupTable[encryption(char)] = char
# Iterate through the CT, two characters at a time (i.e. one byte at a time) and append them to the plaintext
ct = sys.argv[1]
pt = []
for i in range(0, len(ct), 2):
pt.append(lookupTable[ct[i:i+2]])
print(''.join(pt))
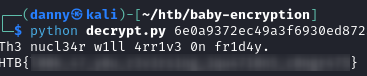
Passing the contents of msg.enc to this script reveals the flag: